Creating webhooks in KeyHub for Splunk
In KeyHub you can send audit log events to applications that can receive webhooks. This guide takes you through the steps to send audit log events from KeyHub to Splunk using webhooks.
In Splunk
Step 1
-
Log in to Splunk
-
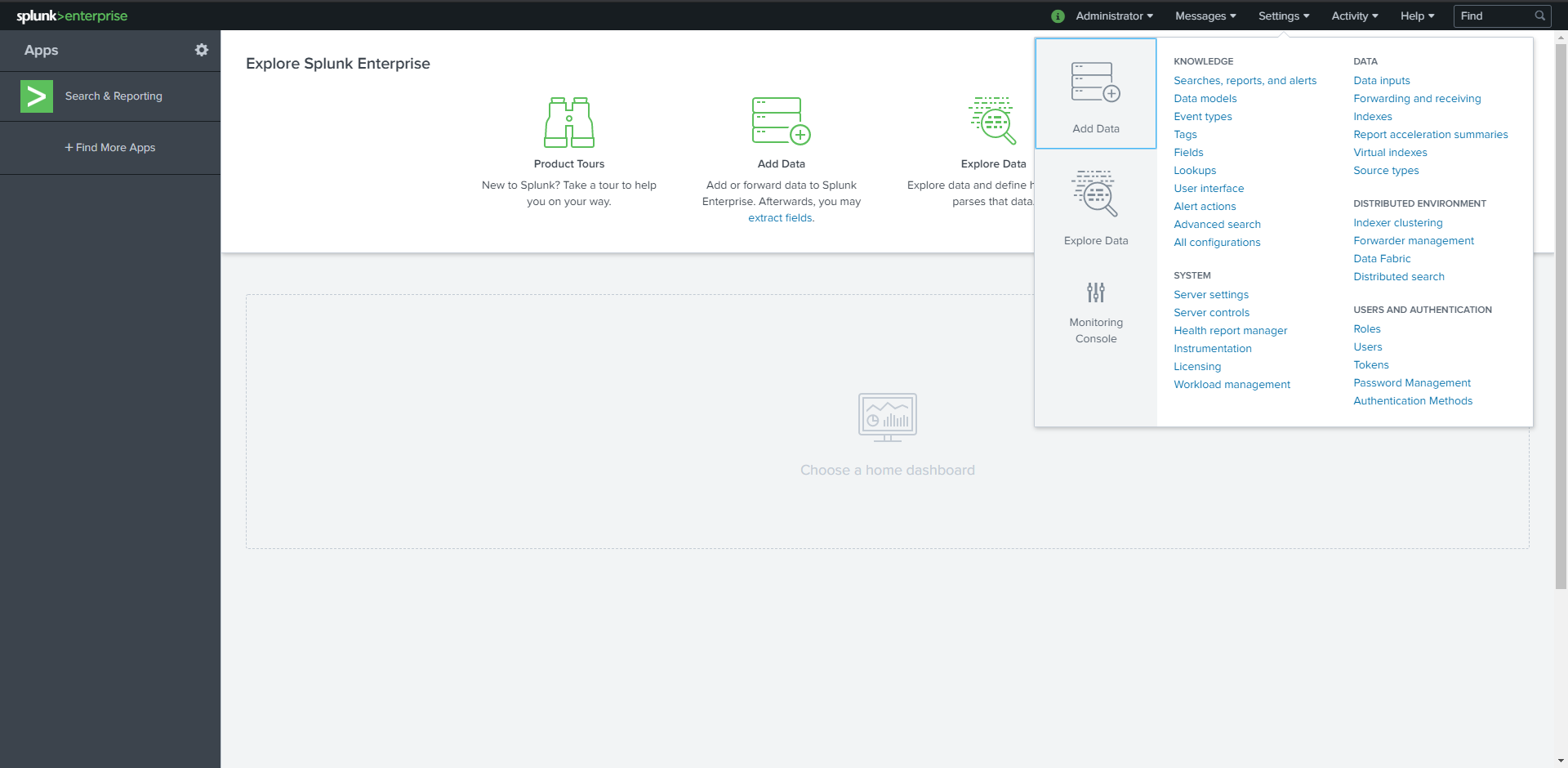
Navigate to Settings
-
Click Data inputs
Step 2
-
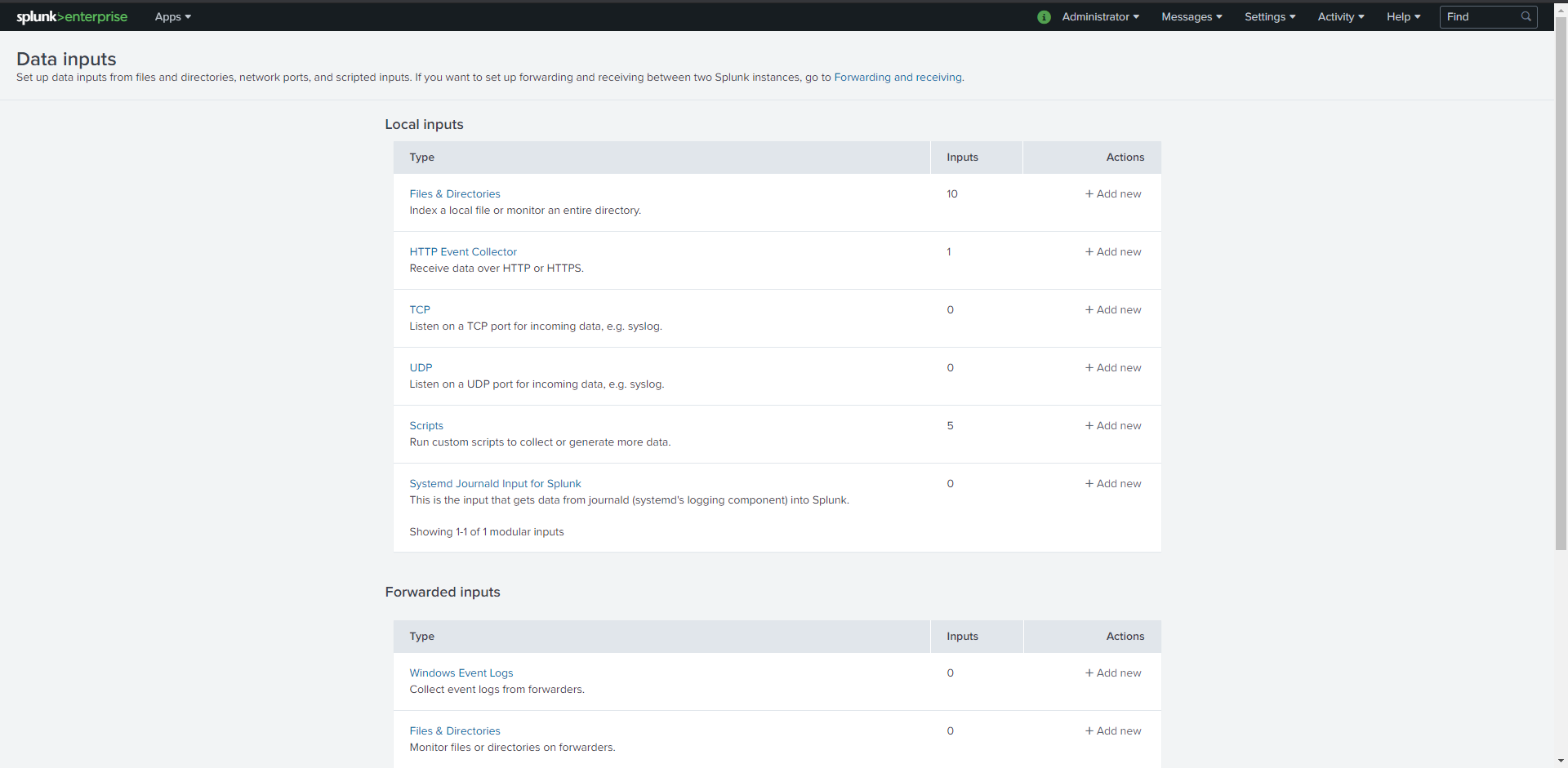
Click HTTP Event Collector
Step 3
-
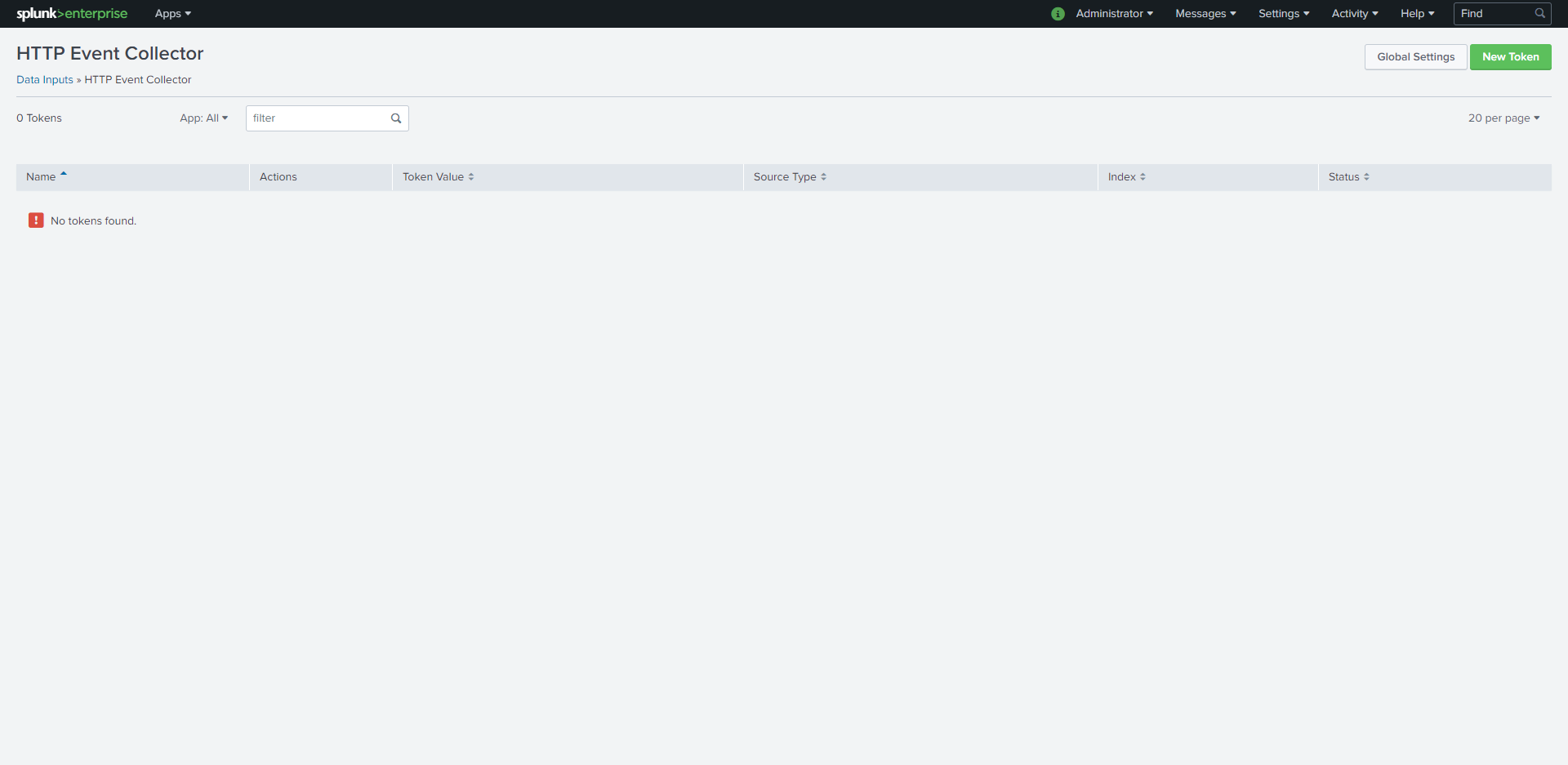
Click New Token
Step 4
-
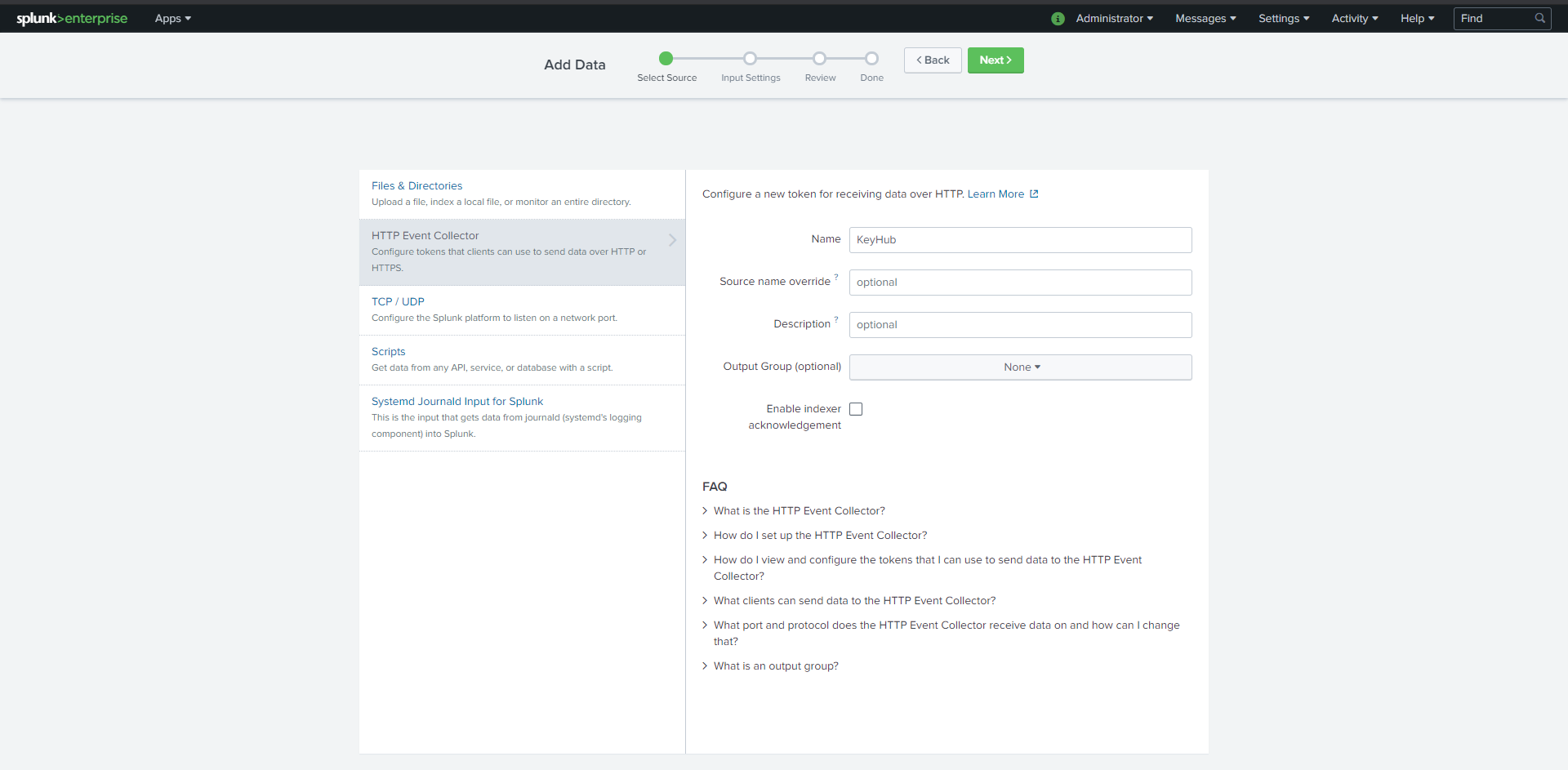
Fill in a Name
-
Click Next>, Review> and Submit> in the following screens
Step 5
-
Navigate back to HTTP Event Collector (Steps 1 and 2)
-
Copy the Token Value
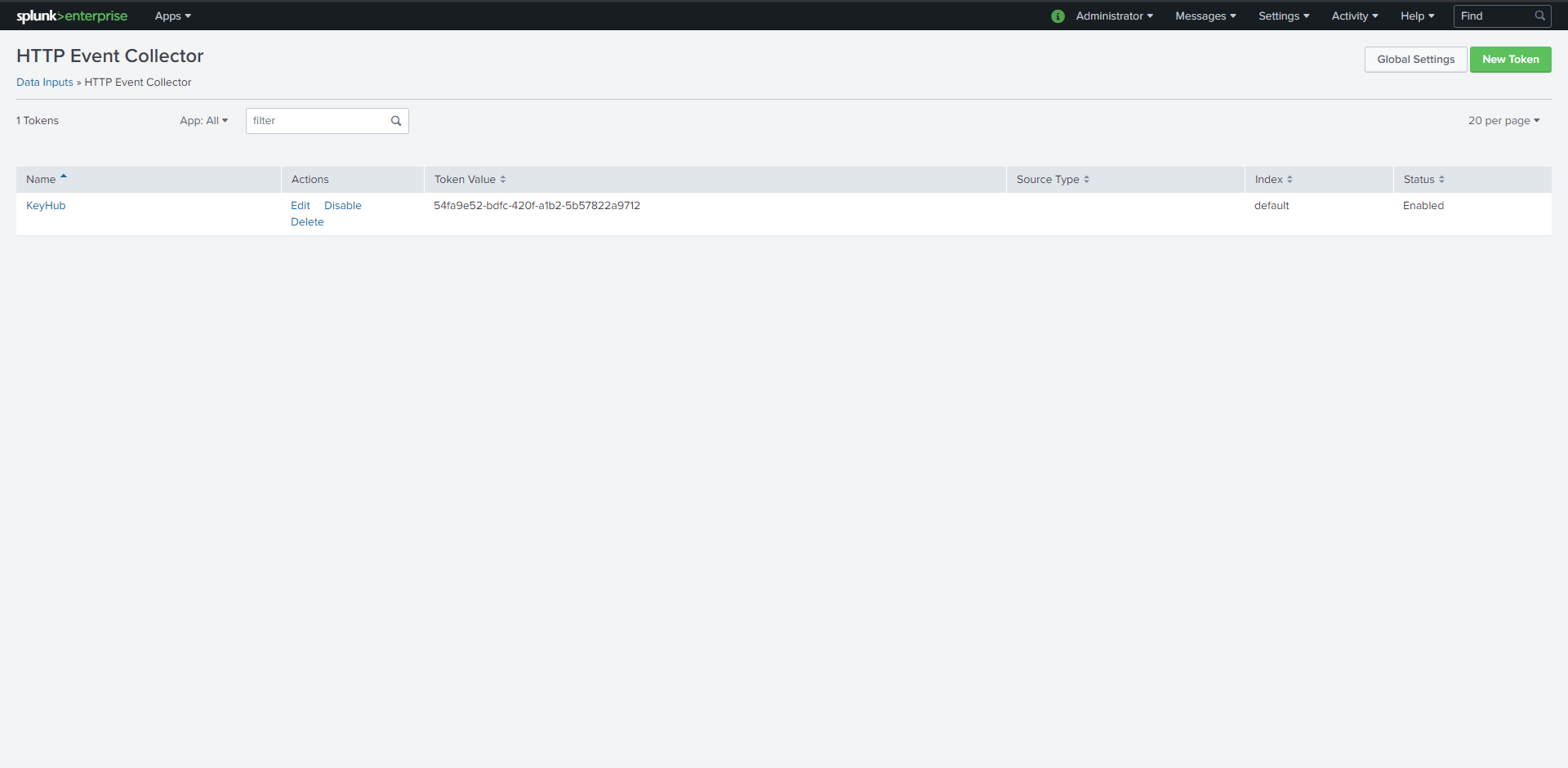
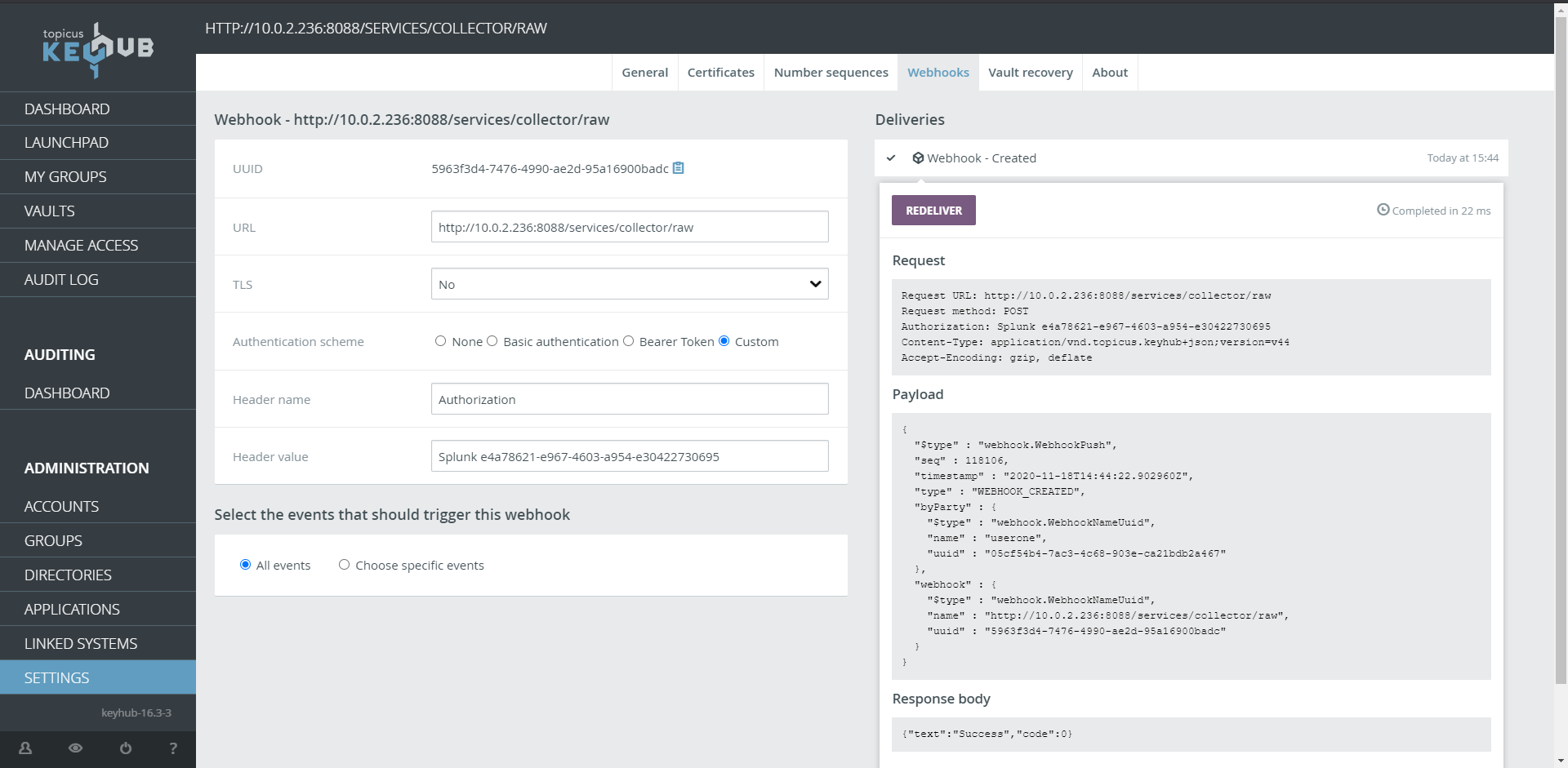
In KeyHub
Step 1
-
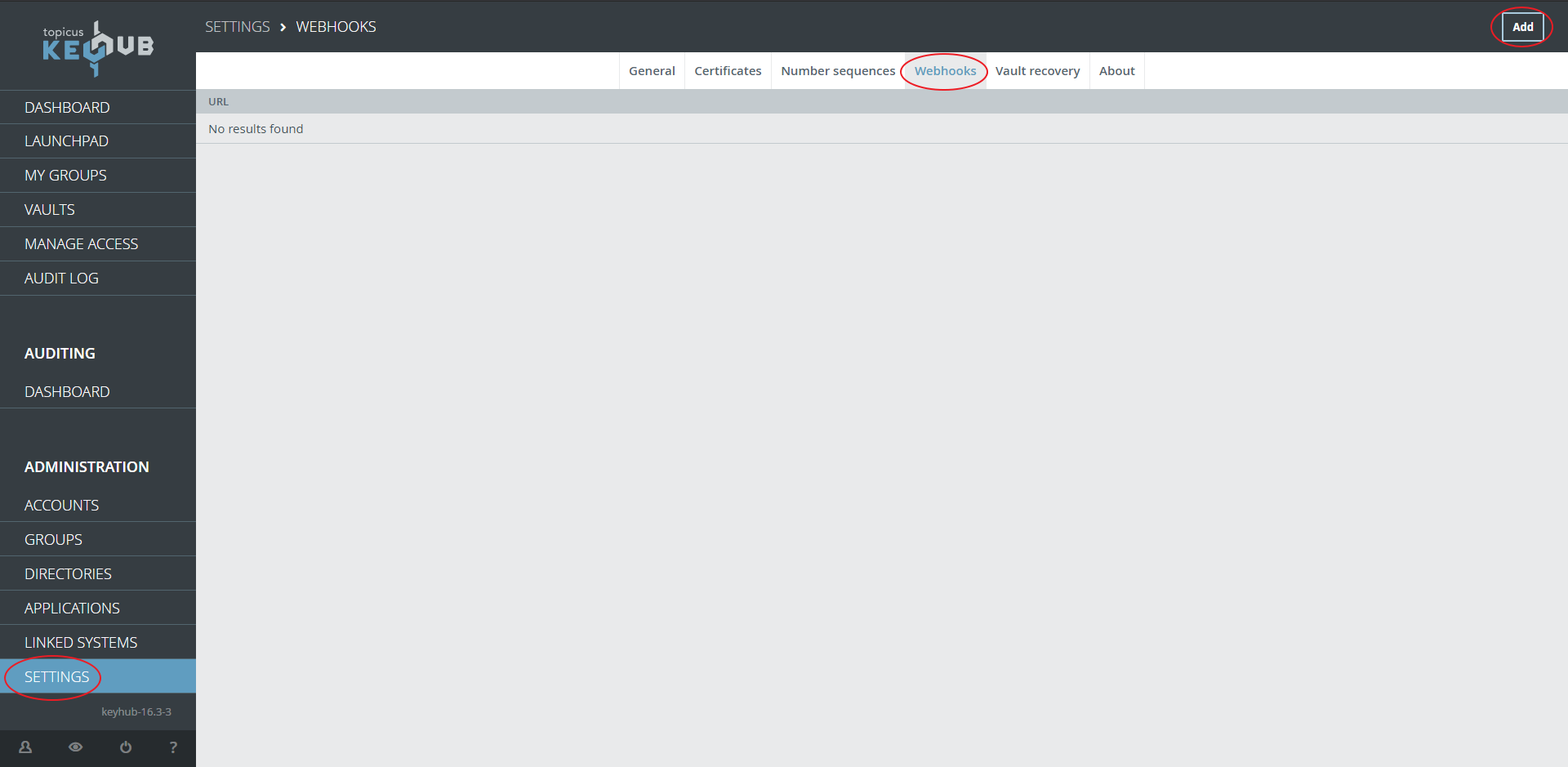
From the menu ADMINISTRATION click GROUPS
-
Select the WEBHOOKS tab
-
Click ADD
Step 2
-
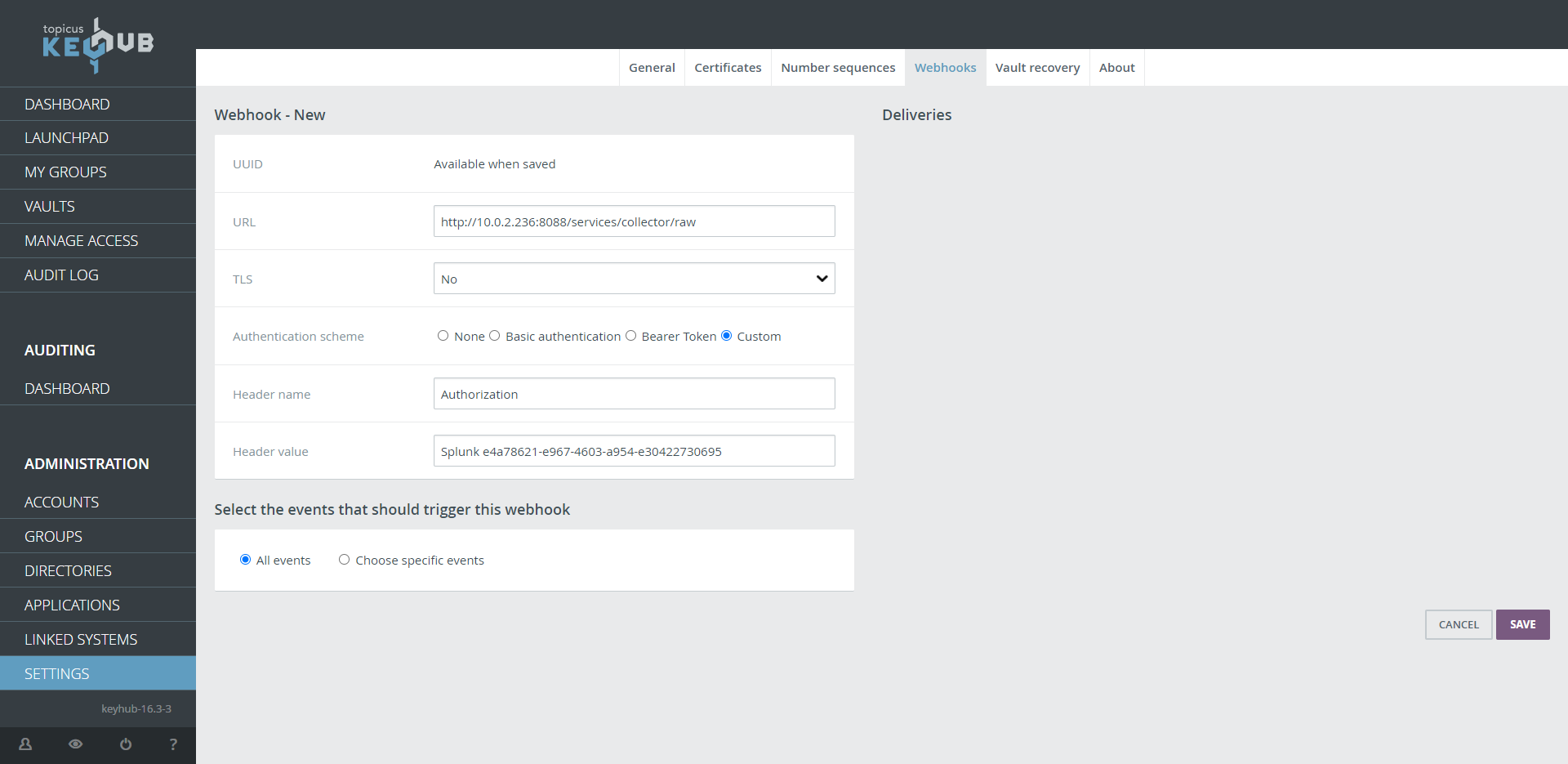
Fill in the URL with <FQDN> your Splunk server
http://<FQDN>:8088/services/collector/raw -
If you have a certificate installed on your Splunk server use TLS Yes
-
Select Custom at Authentication scheme
-
Fill in Authorization at Header name
-
Fill in Splunk <Splunk Token> with <Splunk Token> the copied token from Splunk Step5
-
Select the Events you want to sent to Splunk
-
Click SAVE
Step 3
-
Done
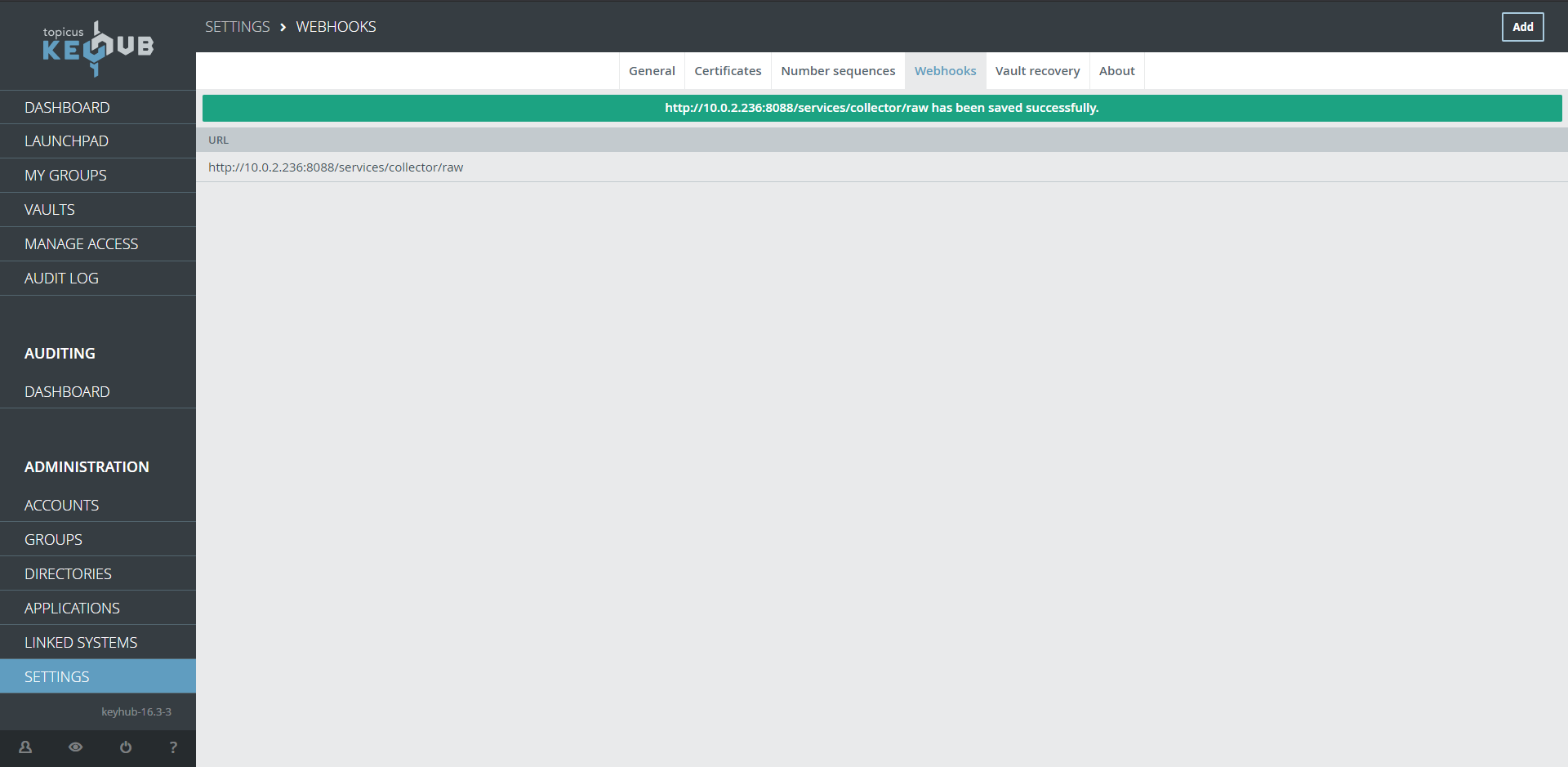
You can review delivered webhooks by clicking on the newly made webhook.
![topicus-keyhub-white.png]](https://portal.topicus-keyhub.com/hs-fs/hubfs/topicus-keyhub-white.png?height=50&name=topicus-keyhub-white.png)