Active Directory Schema Attributes and Classes
Adding a custom attribute
To be able to edit the AD schema you need to run the following command. You only need to do this once. You can run it from an elevated PowerShell Terminal.
PS> regsvr32 schmmgmt.dll
-
run mmc
PS> mmc
The MMC console will pop up. From here you can add the Active Directory Schema snap-in.
-
File > add / remove snap-in
-
Add Active Directory Schema snap-in
-
OK
-
Right click attributes > create attribute
| Read and understand the warning. This one matters. After creating the Class or Attribute you can not modify or delete it! |
-
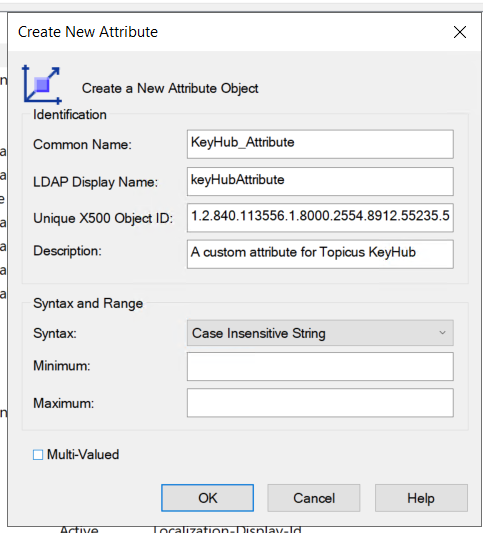
Set your values
Use a generated OID. See Generating an OID.
-
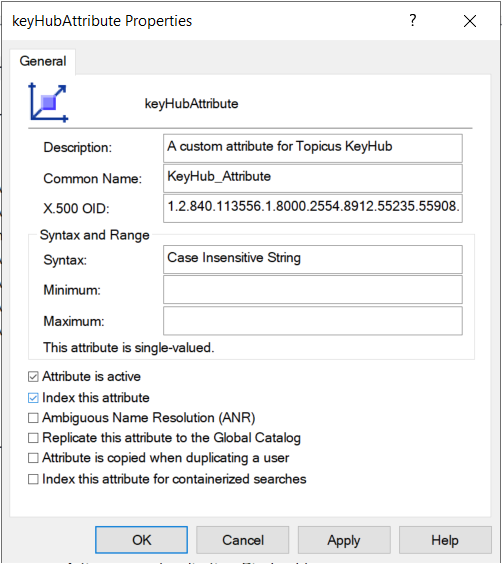
In the container attributes browse to the newly created attribute and open properties.
-
Select "index this attribute"
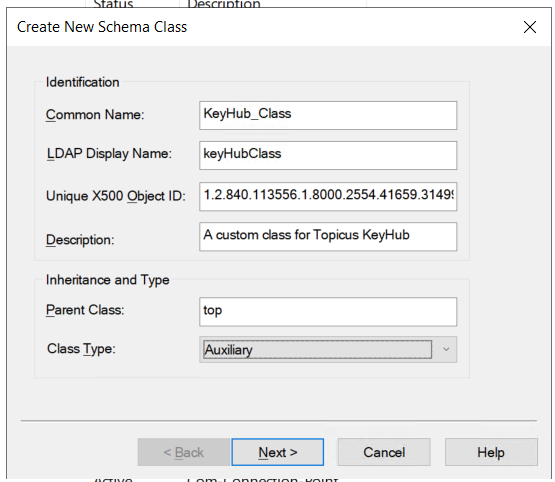
Adding a custom Class
-
Set your values
Use a generated OID. See Generating an OID.
-
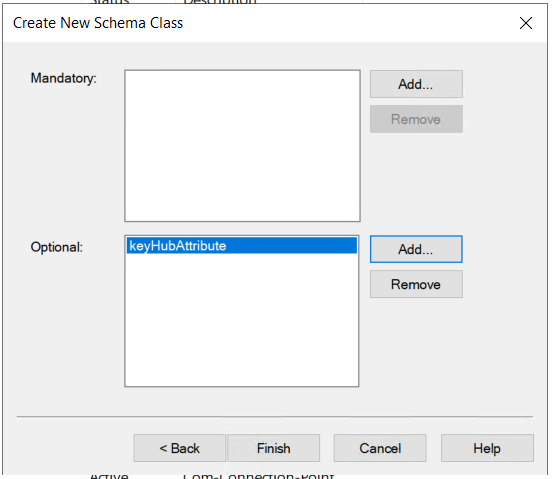
Add custom attributes as needed
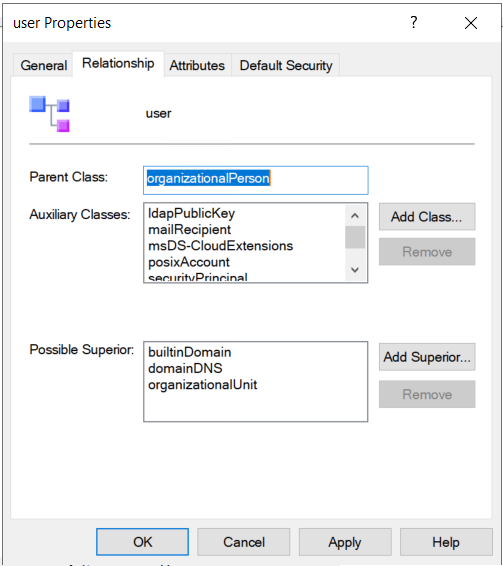
Adding a auxiliary class to another class
-
Open the properties for the higher level class.
-
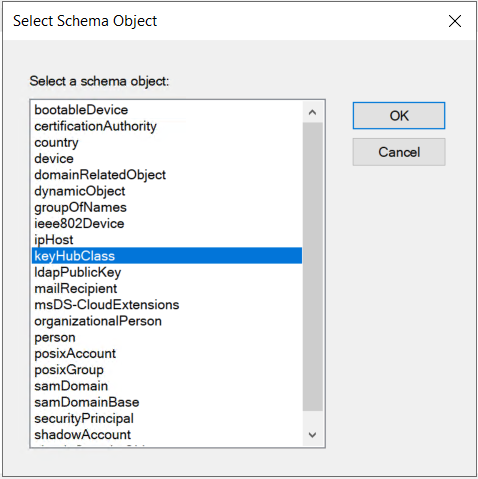
Add the class.
Generating an OID
-
Run the following commands in the terminal. You can copy this code block and paste it in. The Microsoft OID Prefix is used for the automated OID Generator.
$Prefix="1.2.840.113556.1.8000.2554"
$GUID=[System.Guid]::NewGuid().ToString()
$Parts=@()
$Parts+=[UInt64]::Parse($guid.SubString(0,4),"AllowHexSpecifier")
$Parts+=[UInt64]::Parse($guid.SubString(4,4),"AllowHexSpecifier")
$Parts+=[UInt64]::Parse($guid.SubString(9,4),"AllowHexSpecifier")
$Parts+=[UInt64]::Parse($guid.SubString(14,4),"AllowHexSpecifier")
$Parts+=[UInt64]::Parse($guid.SubString(19,4),"AllowHexSpecifier")
$Parts+=[UInt64]::Parse($guid.SubString(24,6),"AllowHexSpecifier")
$Parts+=[UInt64]::Parse($guid.SubString(30,6),"AllowHexSpecifier")
$OID=[String]::Format("{0}.{1}.{2}.{3}.{4}.{5}.{6}.{7}",$prefix,$Parts[0],$Parts[1],$Parts[2],$Parts[3],$Parts[4],$Parts[5],$Parts[6])
$oid
sshPublicKey Attribute for KeyHub provisioning in Active Directory
When enabling Public Key provisioning in a linked directory KeyHub will expect the following Class and Attribute in the AD.
| When adding classes and attributes in Active Directory it is immutable after creation. Make a backup and test in a lab before going to production! |
Attribute:
Common Name: sshPublicKey
X_500 OID: 1.3.6.1.4.1.24552.500.1.1.1.13
Description: 'MANDATORY: OpenSSH Public key'
Syntax: octetString
Multi-Valued: yes
Class:
Common Name: ldapPublicKey
X_500 OID: 1.3.6.1.4.1.24552.500.1.1.2.0
Description: 'MANDATORY: OpenSSH LPK objectclass'
Class type: Auxiliary
Parrent Class: Top
Optional Attribute: sshPublicKey